 | JURA (JURA)ICO The Jura Protocol is a paradigm-shifting suite of four technologies that together form the foundation for a robust new blockchain ecosystem. IMPORTANT: By investing in this business you agree to ourDisclaimer. All information including our rating, is provided merely for informational purposes. CryptoTotem does not provide investment advice. |
Overview
|
What is JURA
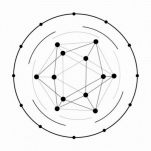
At the core of JURA is the Fusus data structure.
PoVRT, which replaces PoW, is the anti-spamming tool. Each account has its own Fusus chain. Proof of Utility (PoU) then functions as the overseer for the entire system.
JURA will launch using the WebAssembly (WASM) virtual machine.
In the JURA network, the spam attacks could not happen at the first place given the VRF mechanism approach (instead of PoW anti-spam).
The JURA protocol revolves around a novel data structure Fusus which lays down a solid processing infrastructure, and is enhanced with a PoU system that makes self-regulated consensus possible.
DetailsHard cap: 20 000 000 USD | Token infoTicker: JURA |
JURA Roadmap
Whitepaper release
Design prototype of key components
ERC-20 token generation
PoU based consensus framework and FUSUS
Sharding architecture integration
Testnet launch
Embed data storage and data persistent framwork
Smart contract implementation
Virtual machine beta
Mainnet launch
Project team







Advisors








One Response
Benefits of Fusus:
– Transactions are attached algorithmically according to traffic volume, e.g., chain-like ledge in low volume (left), or DAG-like ledger in high volume (right).
– Pruning of transaction histories to save storage and increase lookup efficiency.
– Scalability is enhanced with unmeasurable potential peak.
– PoVRT imposes prolonged spawning time to create a spamming buffer.
Dynamic Monitored and Distributed Sharding (DMDS):
– P2P network traffic partitioning architecture
– Multi-layered design to optimize speed and security
– Parallel processing to further enhance the scalability of the platform
– Compatible with smart contracts, DAG, and existing security designs
– Emergency backup solution to greatly increase system-wide security
Proof of Utility (PoU):
– The first generalized customizable and expandable consensus mechanism that induces self-regulation.
Utility, a pseudo credit score in a decentralized system, measures an abstract quantity of positive contribution to the system’s well-being.
– More variables in addition to stake size are included in estimating the utility.
– Cumulative density functions provide a system-wide assessment of stakes to decide the utility.
– Little-to-no economic incentive to “game” the system and hence strong robustness to malicious attacks.
– Customisable to meet the needs of diverse industries
AI Security:
– Offline learning wallet protection and node detection technology
– Transaction-level filtering
– Malicious node warning
– Increased accuracy over time